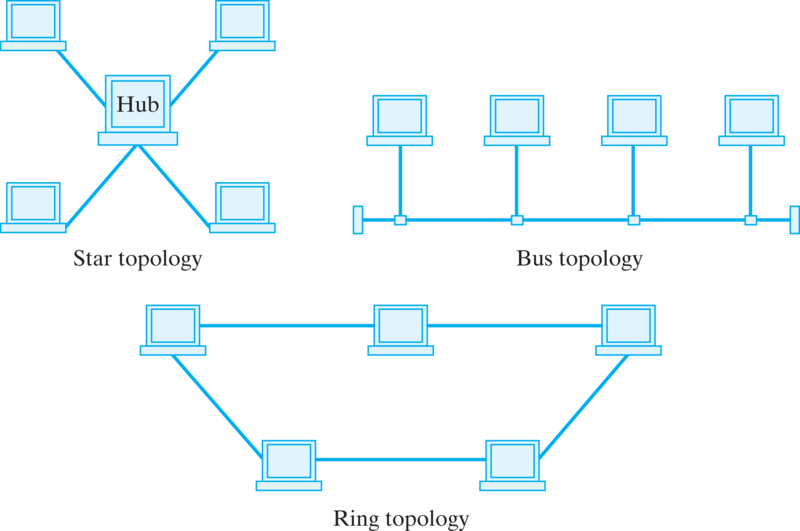
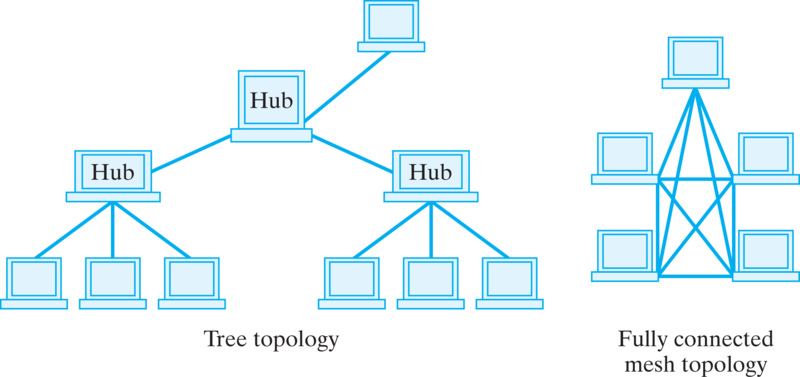
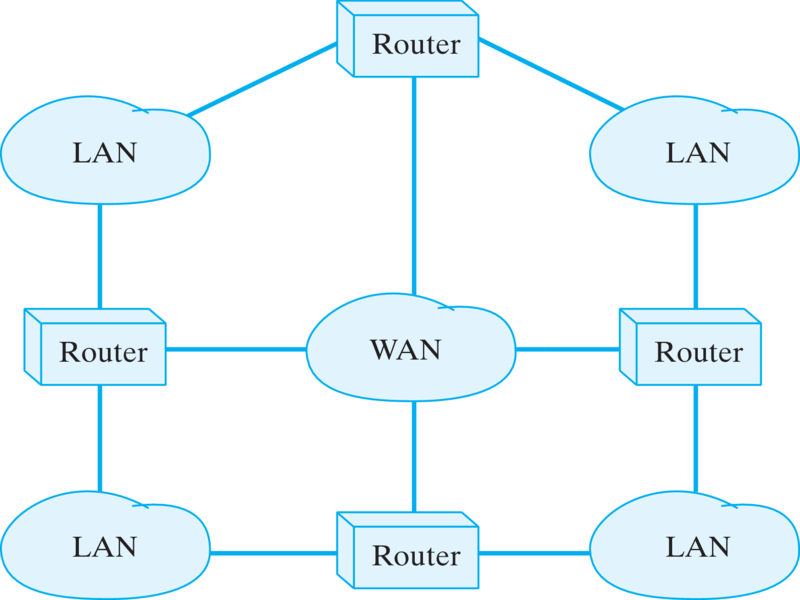
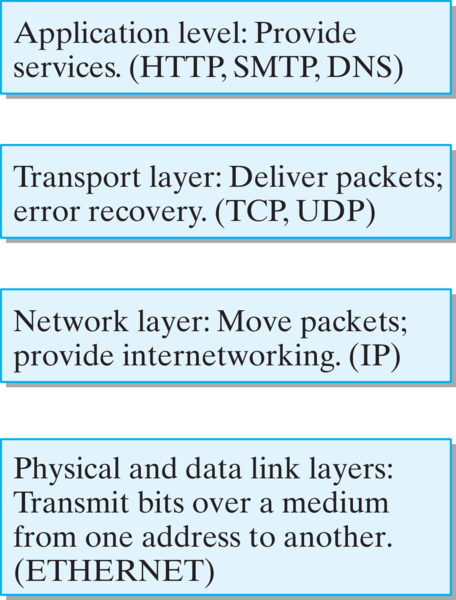
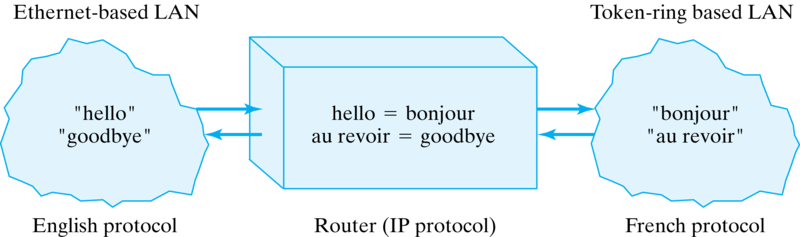
These three examples—HTTP, SMTP, and FTP—are examples of application protocols. They are relatively high-level protocols that support and govern a particular network application, such as e-mail or WWW access. Among the things they determine how we address different computers on the network. For example, the HTTP protocol specifies Web addresses by using a
Uniform Resource Locator (URL). A URL specifies three necessary bits of information: The method used to transfer information (e.g., HTTP or FTP), the address of the host computer (e.g.,
www.prenhall.com), and the path describing where the file is located on the host (
/morelli/index.html):
Similarly, an e-mail address is specified by the SMTP protocol to consist of a local mailbox address (
George.W.Bush) followed by the address of the computer (
mail.whitehouse.gov):
Another good example of an application protocol is the Internet’s
Domain Name System (DNS), which is the system that governs how names, such as
whitehouse.gov and
java.trincoll.edu, can be translated into numeric addresses. In the DNS, each host computer on the Internet is identified with a unique host name—for example,
mail,
java—which is usually made up by the network administrator whose job it is to manage an organization’s network. The DNS divides the entire Internet into a hierarchy of
domains and
subdomains. The generic domains are names like
com,
edu, and
mil, which refer to the type of organization— commercial, educational, and military, respectively. In addition to these there are country domains, such as
fr,
au, and
nz, for France, Australia, and New Zealand. Finally, individuals and organizations can buy their own
domain names, such as
whitehouse,
microsoft, and
trincoll.
What makes the whole system work is that certain computers within the network are designated as DNS servers. It is their role to translate names such as
java.trincoll.edu to numeric addresses whenever they are requested to do so by clients such as the SMTP or the HTTP server. Also, the DNS servers must communicate among themselves to make sure that their databases of names and addresses are up-to-date.