Example 5.3.2. Smurf Attack.
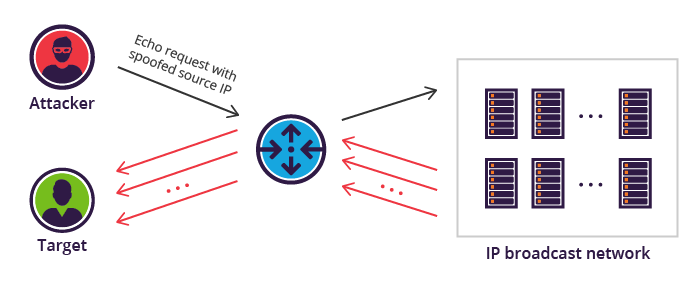
The diagram depicts the mechanics of a Smurf attack. On the left, an "Attacker" sends an "Echo request with spoofed source IP" to a central network device, likely a router, with the spoofed source IP address being that of the "Target," who is also shown on the left, below the attacker. The network device then broadcasts this malicious echo request to an "IP broadcast network," represented on the right as a collection of multiple computer systems. Each system on this broadcast network, upon receiving the echo request, sends an ICMP echo reply. Because the original request’s source IP was spoofed to be the Target’s IP, all these numerous echo replies are directed from the broadcast network, through the central network device, and converge upon the unsuspecting "Target," overwhelming it with traffic. Multiple red arrows illustrate this flood of replies overwhelming the Target.
Smurf DDos Attack by Imperva Incapsula used under CC-BY-SA 4.0
1
commons.wikimedia.org/wiki/File:Ataque_Smurf_DDoS.png2
www.imperva.com/learn/ddos/smurf-attack-ddos/?redirect=Incapsula3
creativecommons.org/licenses/by-sa/4.0/deed.en The Smurf attack is a great example of how spoofed IP addresses can lead to major problems. The Smurf attack is an early type of Distributed Denial of Service attack. An attacker would create an ICMP echo request with the victims IP address as the source address. This echo request would be directed at a broadcast IP address for a subnet. Many of the clients on the subnet would respond the echo request, flooding the victim with responses. The asymmetric nature of this attack, a single packet prompting possibly hundreds of responses, made it particularly hard to deal with. Using a Smurf attack, an attacker could keep a victim pinned down with minimal bandwidth required on their end. Modern clients no longer respond to ICMP echo requests directed at the broadcast, mitigating the risk of this kind of attack.
