Section 1.3 Hacker Culture
The term hacker comes from the sound that programmers would make when typing or hacking away at keyboards. Originally a hacker was anyone who worked feverishly at a problem on a computer and the term cracker was used to define people who attempted to bypass security systems. The distinction was eventually lost and a hacker has come to be the popular term for someone attempting to gain unauthorized access to data. For an interesting glimpse into early hacker culture/reasoning read The Conscience of a Hacker by The Mentor
1
archive.org/stream/The_Conscience_of_a_Hacker/hackersmanifesto.txtSubsection 1.3.1 Hacker Hats
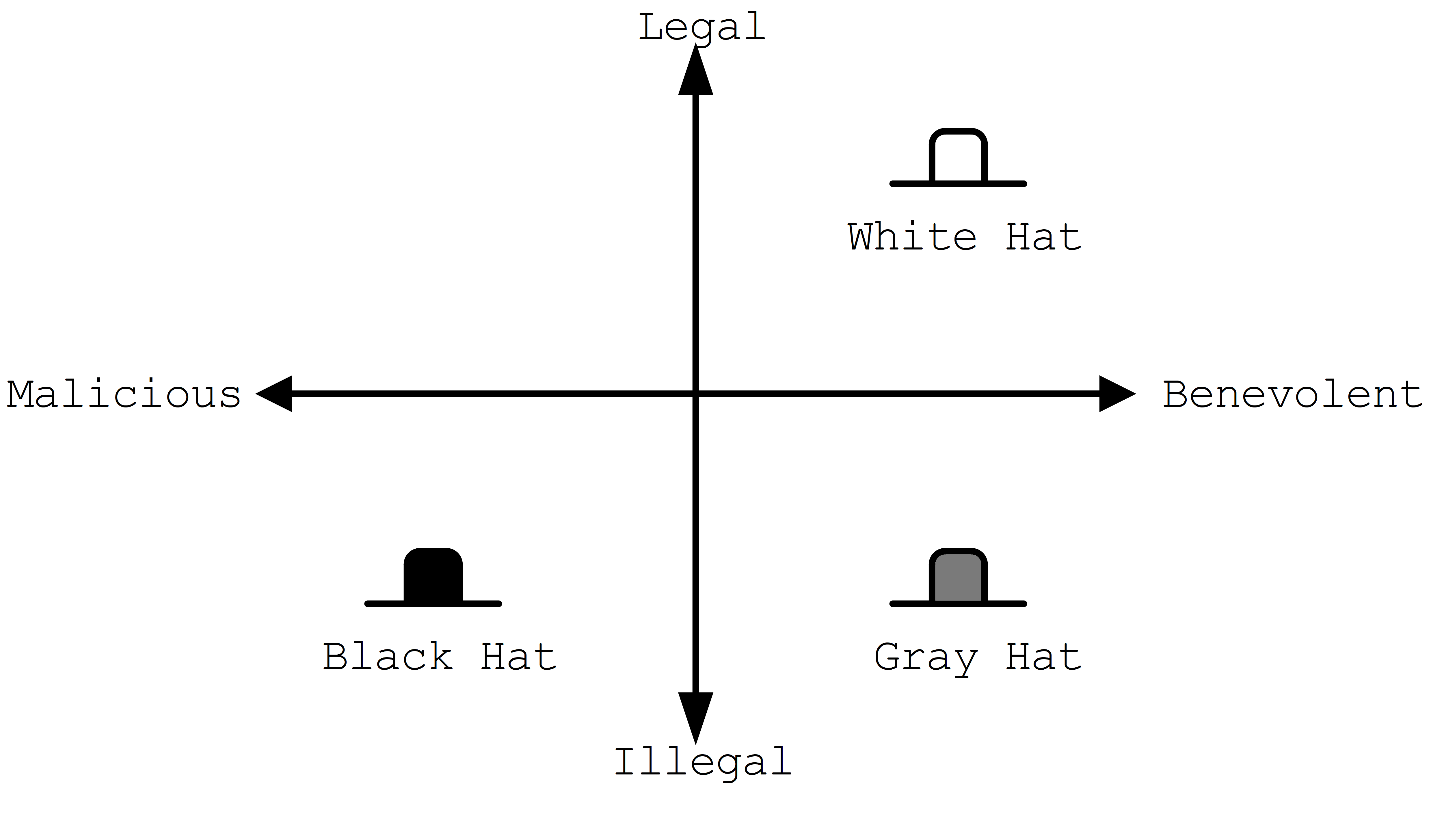
The image, captioned ’Hacker Hats,’ is an alignment chart that classifies different types of hackers using two axes. The horizontal axis ranges from ’Malicious’ on the left to ’Benevolent’ on the right. The vertical axis ranges from ’Legal’ at the top to ’Illegal’ at the bottom, creating four quadrants.
In the top-right quadrant (Legal/Benevolent), a white hat icon is positioned above the label ’White Hat’. In the bottom-left quadrant (Illegal/Malicious), a black hat icon is positioned above the label ’Black Hat’. In the bottom-right quadrant (Illegal/Benevolent), a gray hat icon is positioned above the label ’Gray Hat’. The top-left quadrant (Legal/Malicious) is depicted as empty.
This chart visually categorizes the hacker types based on their ethical stance and legality, corresponding to the classifications detailed in the accompanying text.
An early attempt at classifying hackers involved assigning hat colors according to their motivations. This harkens back to the old western movies where the bad guys wore black hats and the good guys wore white hats. Just as in real life nothing is clearly black and white, as such we’ve laid the traditional roles on a two-axis continuum from malicious to benevolent and illegal to legal.
White Hat: These hackers are typically employed by a company to test the security of their systems. They operate legally with the intent of ultimately improving security.
Black Hat: These hackers operate outside the bounds of the law, and as such are subject to prosecution. Their intent is nefarious usually involving personal profit, malice, or some combination of the two.
Gray Hat: A gray hat hacker operates illegally but ultimately wants to improve the security of the system. They may inform administrators of the details of their breach or they may be acting to force a group to better secure their system. In rare circumstances a gray hat hacker may actually exploit a system for the purposes of hardening it once they have gained administrative access. It should be noted that despite the good intentions, gray hat hackers are still operating illegally and may be subject to prosecution.
There are several more hat distinctions (blue hats, green hats, etc.) with mixed meanings. For example a blue hat may refer to an external entity hired by a company to test the security of a component, as is the case in Microsoft, or it may refer to a hacker motivated by revenge. It is also worth nothing that the second quadrant of our graph is empty, but this does not mean that there aren’t malicious, legal hackers. These may be software developers exploiting legal loopholes or possibly even individuals working for another government engaged in cyber warfare.
You have attempted 1 of 1 activities on this page.
