8.6. Sample Exam Questions¶
- Each packet contains data to be transmitted, along with metadata containing information used for routing the data.
- Each packet contains an encrypted version of the data to be transmitted, along with metadata containing the key needed to decrypt the data.
- Each packet contains only the metadata used to establish a direct connection so that the data can be transmitted.
- Each packet contains multiple data files bundled together, along with metadata describing how to categorize each data file.
Q-1: AP 2021 Sample Question: Which of the following best explains how data is typically assembled in packets for transmission over the Internet?
- 1001 0100
- 1001 0111
- 1101 0100
- 1101 0111
Q-2: AP 2021 Sample Question: Each student that enrolls at a school is assigned a unique ID number, which is stored as a binary number. The ID numbers increase sequentially by 1 with each newly enrolled student. If the ID number assigned to the last student who enrolled was the binary number 1001 0011, what binary number will be assigned to the next student who enrolls?
- That is correct!
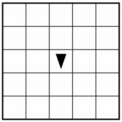
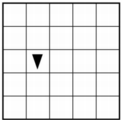
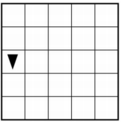
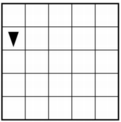
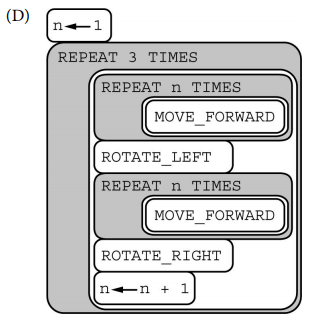
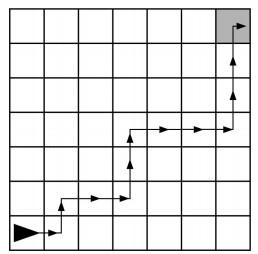
Q-3: AP 2021 Sample Question: The following grid contains a robot represented as a triangle. The robot is initially facing right. Which of the following code segments can be used to move the robot to the gray square along the path indicated by the arrows
- A vulnerability in the device’s software is exploited to gain unauthorized access to other devices on the user’s home network.
- This sounds like a hacking attack, not a phishing attack.
- A vulnerability in the device’s software is exploited to install software that reveals the user’s password to an unauthorized individual.
- This sounds like a hacking attack, not a phishing attack.
- The user is sent an e-mail appearing to be from the manufacturer, asking the user to confirm the account password by clicking on a link in the e-mail and entering the password on the resulting page.
- Yes, a phishing attack is usually an e-mail that tries to fool people into revealing private information like passwords.
- The user’s account is sent an overwhelming number of messages in an attempt to disrupt service on the user’s home network.
- This sounds like a denial of service attack, not a phishing attack.
Q-4: AP 2021 Practice Question: A user purchased a new smart home device with embedded software andconnected the device to a home network. The user then registered the devicewith the manufacturer, setting up an account using a personal e-mail andpassword. Which of the following explains how a phishing attack could occuragainst the user of the smart home device?
- A school allows students to bring a graphing calculator from home to complete in-class mathematics assignments.
- A school allows students to bring a tablet computer to class every day to participate in graded quizzes.
- A school provides a laptop or tablet computer to all students enrolled at the school.
- A school recommends that all students purchase a computer with as much processing speed as possible so that projects run faster.
Q-5: AP 2021 Sample Question: Which of the following school policies is most likely to have a positive impact on the digital divide?
- II only
- I and II only
- I and III only
- II and III only
Q-6:
AP 2021 Sample Question: In a certain country, a person must be at least 16 years old to drive a car and must be at least 18 years old to vote. The variable age represents the age of a person as an integer. Which of the following expressions evaluates to true if the person is old enough to drive but not old enough to vote, and evaluates to false otherwise?
I. (age ≥ 16) AND (age ≤ 18)
II. (age ≥ 16) AND (NOT(age ≥ 18))
III. (age < 18) AND (NOT(age < 16))
- Each employee for a company is issued a USB device that contains a unique token code. To log into a company computer, an employee must insert the USB device into the computer and provide a correct password.
- After logging into an account from a new device, a user must enter a code that is sent via e-mail to the e-mail address on file with the account.
- In order to log into an account, a user must provide both a password and a fingerprint that is captured using the user’s device.
- When a user enters an incorrect password more than two times in a row, the user is locked out of the account for 24 hours.
Q-7: AP 2021 Sample Question: A Web site uses several strategies to prevent unauthorized individuals from accessing user accounts. Which of the following is NOT an example of multifactor authentication?
- Step 3: Increase the value of position by 1.
Step 4: Repeat steps 2 and 3 until the value of count is greater than 100. - Step 3: Increase the value of position by 1.
Step 4: Repeat steps 2 and 3 until the value of position is greater than n. - Step 3: Repeat step 2 until the value of count is greater than 100.
Step 4: Increase the value of position by 1. - Step 3: Repeat step 2 until the value of position is greater than n.
Step 4: Increase the value of count by 1.
Q-8: AP 2021 Sample Question: A list of numbers has n elements, indexed from 1 to n. The following algorithm is intended to display the number of elements in the list that have a value greater than 100. The algorithm uses the variables count and position. Steps 3 and 4 are missing.Step 1: Set count to 0 and position to 1.Step 2: If the value of the element at index position is greaterthan 100, increase the value of count by 1.Step 3: (missing step)Step 4: (missing step)Step 5: Display the value of count.Which of the following could be used to replace steps 3 and 4 so that the algorithm works as intended?
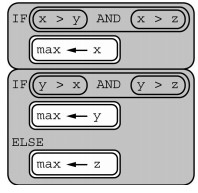
- x = 1, y = 2, z = 3
- x = 1, y = 3, z = 2
- x = 2, y = 3, z = 1
- x = 3, y = 2, z = 1
Q-9: AP 2021 Sample Question: The following code segment is intended to set max equal to the maximum value among the integer variables x, y, and z. The code segment does not work as intended in all cases.Which of the following initial values for x, y, and z can be used to show that the code segment does not work as intended?
- Determining the likelihood that the photo is a picture of the sky
- Determining the likelihood that the photo was taken at a particular public event
- Determining the number of people that appear in the photo
- Determining the usability of the photo for projection onto a particular color background
Q-10: AP 2021 Sample Question: A digital photo file contains data representing the level of red, green, and blue for each pixel in the photo. The file also contains metadata that describe the date andgeographic location where the photo was taken. For which of the following goals would analyzing the metadata be more appropriate than analyzing the data?
- Changing line 6 to IF(item = count)
- Changing line 6 to IF(myList[item] = val)
- Moving the statement in line 5 so that it appears between lines 2 and 3
- Moving the statement in line 11 so that it appears between lines 9 and 10
Q-11: AP 2021 Sample Question: The following procedure is intended to return the number of times the value val appears in the list myList. The procedure does not work as intended.Line 1: PROCEDURE countNumOccurences(myList, val)Line 2: {Line 3: FOR EACH item IN myListLine 4: {Line 5: count 0Line 6: IF(item = val)Line 7: {Line 8: count count + 1Line 9: }Line 10: }Line 11: RETURN(count)Line 12: }Which of the following changes can be made so that the procedure will work as intended?
- 60 seconds
- Since there are only 2 processors available, one of them must do 2 tasks. Combining any 2 of the X, Y, and Z tasks will add up to more than 70 seconds.
- 70 seconds
- Since there are only 2 processors available, one of them must do 2 tasks. Combining any 2 of the X, Y, and Z tasks will add up to more than 70 seconds.
- 80 seconds
- If you did process X on processor 1 at the same time as doing process Y and then Z on processor 2, processor 1 would be done in 60 seconds and processor 2 would be done in 80 sections (50+30).
- 90 seconds
- This would be true if you did process X and Y on processor 1 (60+30 = 90 seconds) but there is a shorter execution time available if you combined processes in another way.
Q-12: AP 2021 Sample Question: A certain computer has two identical processors that are able to run in parallel.Each processor can run only one process at a time, and each process must beexecuted on a single processor. The following table indicates the amount of timeit takes to execute each of three processes on a single processor. Assume thatnone of the processes are dependent on any of the other processes.ProcessExecution Time on Either ProcessorX 60 secondsY 30 secondsZ 50 secondsWhich of the following best approximates the minimum possible time to execute all three processes when the two processors are run in parallel?
- 10
- 50
- 250
- 500
Q-13: AP 2021 Sample Question: A sorted list of numbers contains 500 elements. Which of the following is closest to the maximum number of list elements that will be examined when performing a binary search for a value in the list?
- A list of common issues and whether each issue requires a human representative
- A list of common keywords or phrases and a corresponding issue for each keyword or phrase
- A list of computers the company owns and the computers’ corresponding IP addresses
- A list of human representatives and the corresponding department for each representative
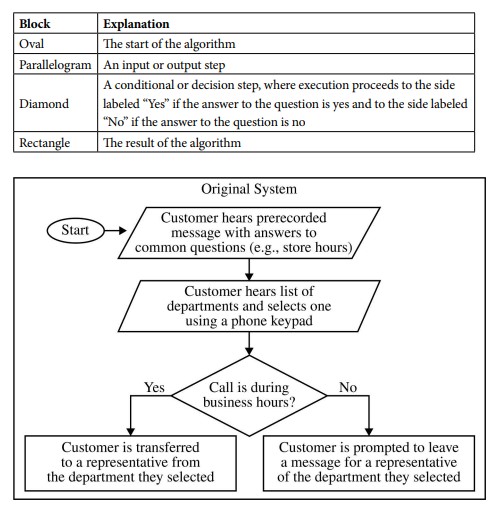
Q-14: Questions 14–16 refer to the information below. Note: This is a representative sample of questions related to the reading passage. There will be five single-select multiple-choice questions related to a reading passage on the AP Exam.A chain of retail stores uses software to manage telephone calls from customers. The system was recently upgraded. Customers interacted with the original system using their phone keypad. Customers interact with the upgraded system using their voice.The upgraded system (but not the original system) stores all information from the calling session in a database for future reference. This includes the customer’s telephone number and any information provided by the customer (name, address, order number, credit card number, etc.).The original system and the upgraded system are described in the following flowcharts. Each flowchart uses the following blocks.AP 2021 Sample Question: The upgraded system uses a directory containing additional information not supplied by the customer. The directory is used to help direct calls effectively. Which of the following is LEAST likely to be included in the directory?
- Human representatives will not be needed to respond to some inquiries.
- The company will be able to provide a human representative for any incoming call.
- Customers are likely to spend less time listening to information not relevant to their issue.
- Customers will be unable to mistakenly select the incorrect department for their particular issue.
Q-15: AP 2021 Sample Question: Of the following potential benefits, which is LEAST likely to be provided by the upgraded system?
- Customers’ personal information could be compromised if an unauthorized individual gains access to the call session database.
- Storing information in the call session database makes it easy for individuals to trick the system using malicious links.
- The system design increases the chance that customers will unknowingly install malware on their devices that will share their data with unauthorized individuals.
- The system design makes it easy for unauthorized individuals to acquire customers’ private encryption keys.
Q-16: AP 2021 Sample Question: Which of the following is the most likely data privacy concern of the upgraded system?
Q-17: AP 2021 Sample Question: Consider the following procedure.Procedure CallExplanationdrawCircle(xPos, yPos, rad)Draws a circle on a coordinate grid with center (xPos, yPos) and radius radThe drawCircle procedure is to be used to draw the following figure on a coordinate grid.Which of the following code segments can be used to draw the figure?Select two answers.
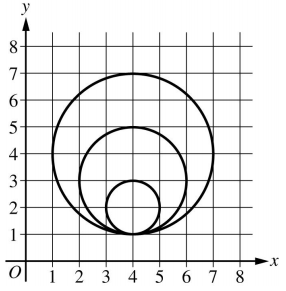
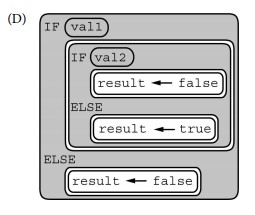
Q-18: AP 2021 Sample Question: In the following statement, val1, val2, and result are Booleanvariables. Which of the following code segments produce the same result as the statement above for all possible values of val1 and val2?Select two answers.

- 2 times as many values can be represented.
- Not quite. Adding just one extra bit (binary digit) allows for 2 times as many values. In this case you are adding 32 extra bits.
- 32 times as many values can be represented.
- Not quite
- 2^32 times as many values can be represented.
- This is correct!
- 32^2 times as many values can be represented.
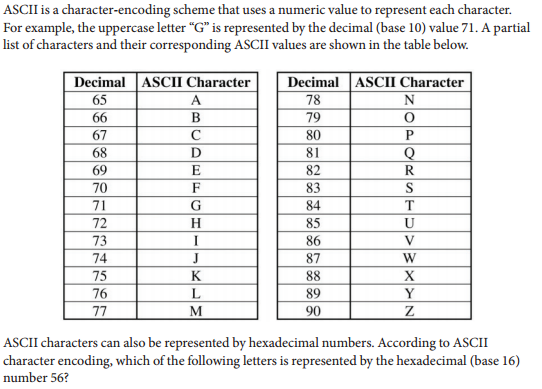
Q-19: A video-streaming Web site uses 32-bit integers to count the number of times each video has been played. In anticipation of some videos being played more times than can be represented with 32 bits, the Web site is planning to change to 64-bit integers for the counter. Which of thefollowing best describes the result of using 64-bit integers instead of 32-bit integers?
- A
- L
- V
- This is correct because 56 in base 16 (hex) is 5x161 + 6 x 160 = 86 in decimal which is the code for the letter V.
- Y
Q-20:
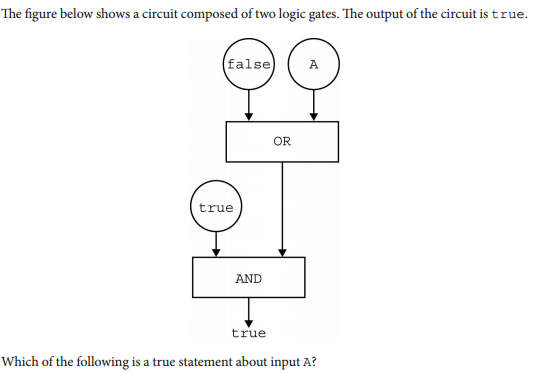
- Input A must be true.
- This is correct!
- Input A must be false.
- Input A can be either true or false.
- There is no possible value of Input A that will cause the circuit to have the output true.
Q-21:
- Computer simulations can only be built after the real-world object or system has been created.
- Computer simulations only run on very powerful computers that are not available to the general public.
- Computer simulations usually make some simplifying assumptions about the real-world object or system being modeled.
- This is correct
- It is difficult to change input parameters or conditions when using computer simulations.
Q-22: Which of the following statements describes a limitation of using a computer simulation to model a real-world object or system?
- Approximately how many miles did the animal travel in one week?
- Does the animal travel in groups with other tracked animals?
- Do the movement patterns of the animal vary according to the weather?
- This is correct.
- In what geographic locations does the animal typically travel?
Q-23: Biologists often attach tracking collars to wild animals. For each animal, the following geolocation data is collected at frequent intervals.The timeThe date The location of the animalWhich of the following questions about a particular animal could NOT be answered using only the data collected from the tracking collars?
- To determine the users who post messages most frequently
- To determine the time of day that the site is most active
- It would actually be better analyze the metadata for this.
- To determine the topics that many users are posting about
- That is correct!
- To determine which posts from a particular user have received the greatest number of comments
Q-24: A certain social media Web site allows users to post messages and to comment on other messages that have been posted. When a user posts a message, the message itself is considered data. In addition to the data, the site stores the following metadata.The time the message was postedThe name of the user who posted the messageThe names of any users who comment on the message and the times the comments were madeFor which of the following goals would it be more useful to analyze the data instead of themetadata?
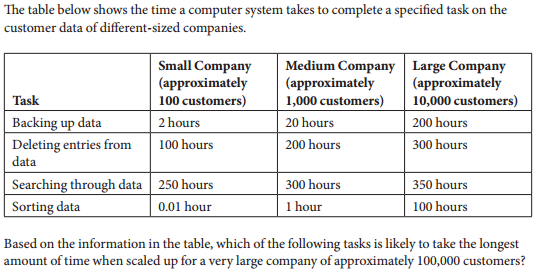
- Backing up data
- Not quite - According to the table, backing up data for a company with 100,000 would take over 2,000 hours (200 x 10). Even though that's a long time, there is another task that would take even longer.
- Deleting entries from data
- Nice try, but according to this table deleting entries for a company with approximately 100,000 customers would only take 400 hours.
- Searching through data
- Nice try, but the question is asking about 100,000 customers.
- Sorting data
- That is correct!
Q-25:
- Data compression is only useful for files being transmitted over the Internet.
- No matter what compression technique is used, once a data file is compressed, it cannot be restored to its original state.
- Sending a compressed version of a file ensures that the contents of the file cannot be intercepted by an unauthorized user.
- There are trade-offs involved in choosing a compression technique for storing and transmitting data.
- That's correct!
Q-26: Which of the following is a true statement about data compression?
- First, change all occurrences of “goats” to “sheep.”
Then, change all occurrences of “sheep” to “goats.” - First, change all occurrences of “goats” to “sheep.”
Then, change all occurrences of “sheep” to “goats.”
Last, change all occurrences of “foxes” to “sheep.” - First, change all occurrences of “goats” to “foxes.”
Then, change all occurrences of “sheep” to “goats.”
Last, change all occurrences of “foxes” to “sheep.” - That's correct!
- First, change all occurrences of “goats” to “foxes.”
Then, change all occurrences of “foxes” to “sheep.”
Last, change all occurrences of “sheep” to “goats.”
Q-27: A programmer completes the user manual for a video game she has developed and realizes she has reversed the roles of goats and sheep throughout the text. Consider the programmer’s goal of changing all occurrences of “goats” to “sheep,” and all occurrences of “sheep” to “goats.” The programmer will use the fact that the word “foxes” does not appear anywhere in the original text.Which of the following algorithms can be used to accomplish the programmer’s goal?
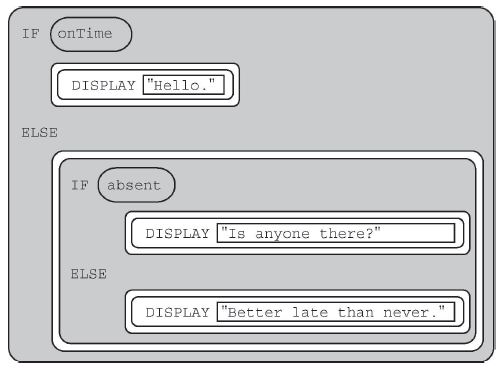
- Is anyone there?
- This would only display if absent was true, but absent is false.
- Better late than never.
- That's correct!
- Hello. Is anyone there?
- Hello would only display if onTime was true, but onTime is false.
- Hello. Better late than never.
- Hello would only display if onTime was true, but onTime is false.
Q-28: Consider the code segment below.If the variables onTime and absent both have the value false, what is displayed as a result of running the code segment?
Q-29: The program segment below is intended to move a robot in a grid to a gray square. The program segment uses the procedure GoalReached, which evaluates to true if the robot is in the gray square and evaluates to false otherwise. The robot in each grid is represented as a triangle and is initially facing left. The robot can move into a white or gray square, but cannot move into a black region.For which of the following grids does the program NOT correctly move the robot to the gray square?

- When the problem can be solved in a reasonable time and an approximate solution is acceptable.
- When the problem can be solved in a reasonable time and an exact solution is needed.
- When the problem cannot be solved in a reasonable time and an approximate solution is acceptable.
- When the problem cannot be solved in a reasonable time and an exact solution is needed.
Q-30: Under which of the following conditions is it most beneficial to use a heuristic approach to solve a problem?
- Algorithm A always calculates the correct average, but Algorithm B does not.
- Algorithm B always calculates the correct average, but Algorithm A does not.
- Both Algorithm A and Algorithm B always calculate the correct average.
- Neither Algorithm A nor Algorithm B calculates the correct average.
Q-31: There are 32 students standing in a classroom. Two different algorithms are given for findingthe average height of the students.Algorithm AStep 1: All students stand.Step 2: A randomly selected student writes his or her height on a card and is seated.Step 3: A randomly selected standing student adds his or her height to the value on the card,records the new value on the card, and is seated. The previous value on the card is erased.Step 4: Repeat step 3 until no students remain standing.Step 5: The sum on the card is divided by 32. The result is given to the teacher.Algorithm BStep 1: All students stand.Step 2: Each student is given a card. Each student writes his or her height on the card.Step 3: Standing students form random pairs at the same time. Each pair adds the numberswritten on their cards and writes the result on one student’s card; the other student isseated. The previous value on the card is erased.Step 4: Repeat step 3 until one student remains standing.Step 5: The sum on the last student’s card is divided by 32. The result is given to the teacher.Which of the following statements is true?
Q-32:
The following question uses a robot in a grid of squares. The robot is represented as a triangle, which is initially in the bottom left square of the grid and facing right.
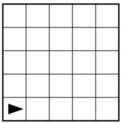
Consider the following code segment, which moves the robot in the grid.
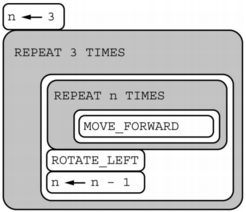
Which of the following shows the location of the robot after running the code segment?
Q-33:
The figure below shows a robot in a grid of squares. The robot is represented as a triangle, which is initially facing upward. The robot can move into a white or gray square but cannot move into a black region.
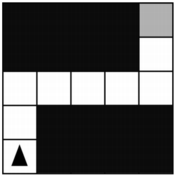
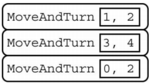
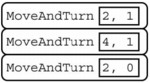
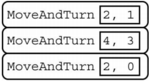
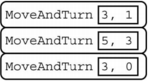
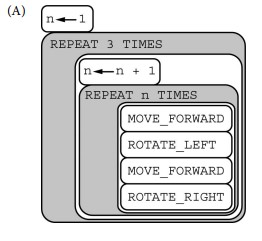
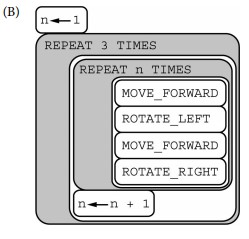
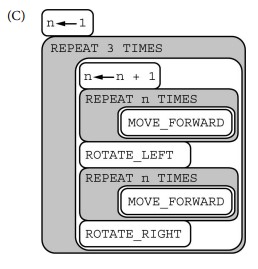
Consider the procedure MoveAndTurn below.
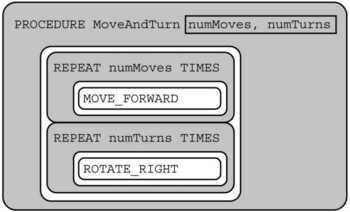
Which of the following code segments will move the robot to the gray square?
Q-34:
A summer camp offers a morning session and an afternoon session. The list morningList contains the names of all children attending the morning session, and the list afternoonList contains the names of all children attending the afternoon session.
Only children who attend both sessions eat lunch at the camp. The camp director wants to create lunchList, which will contain the names of children attending both sessions.
The following code segment is intended to create lunchList, which is initially empty. It uses the procedure IsFound (list, name), which returns true if name is found in list and returns false otherwise.
FOR EACH child IN morningList
{ <MISSING CODE>
}
Which of the following could replace <MISSING CODE> so that the code segment works as intended?
IF (IsFound (afternoonList, child))
{
APPEND (lunchList, child)
}IF (IsFound (lunchList, child))
{
APPEND (afternoonList, child)
}IF (IsFound (morningList, child))
{
APPEND (lunchList, child)
}IF ((IsFound (morningList, child)) OR
(IsFound (afternoonList, child)))
{
APPEND (lunchList, child)
}- The number 0 is displayed.
- The number 6 is displayed.
- The number 10 is displayed.
- Nothing is displayed; the program results in an infinite loop.
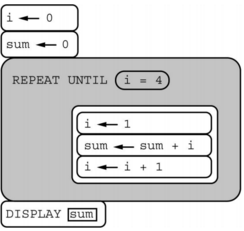
Q-35: Consider the following program code.Which of the following best describes the result of running the program code?
- (onFloor1 AND callTo2) AND (onFloor2 AND callTo1)
- (onFloor1 AND callTo2) OR (onFloor2 AND callTo1)
- That's correct!
- (onFloor1 OR callTo2) AND (onFloor2 OR callTo1)
- (onFloor1 OR callTo2) OR (onFloor2 OR callTo1)
Q-36: An office building has two floors. A computer program is used to control an elevator that travels between the two floors. Physical sensors are used to set the following Boolean variables.The elevator moves when the door is closed and the elevator is called to the floor that it is not currently on. Which of the following Boolean expressions can be used in a selection statement to cause the elevator to move?

- about.example.com
- example.co.uk
- example.com.org
- example.org
Q-37: According to the domain name system (DNS), which of the following is a subdomain of the domain example.com?
- I
- II
- I and II
- Neither I nor II
Q-38: Which of the following are true statements about digital certificates in Web browsers? I. Digital certificates are used to verify the ownership of encrypted keys used in secured communication. II. Digital certificates are used to verify that the connection to a Web site is fault tolerant.
- An algorithm that, given two integers, displays the greater of the two integers
- An algorithm that, given a list of integers, displays the number of even integers in the list
- An algorithm that, given a list of integers, displays only the negative integers in the list
- An algorithm that, given a list of integers, displays the sum of the integers in the list
Q-39: Which of the following algorithms require both selection and iteration?Select two answers.
Q-40: A teacher uses the following program to adjust student grades on an assignment by adding 5 points to each student’s original grade. However, if adding 5 points to a student’s original grade causes the grade to exceed 100 points, the student will receive the maximum possible score of 100 points. The students’ original grades are stored in the list gradeList, which is indexed from 1 to n.
i ← 1
REPEAT n TIMES
{
<MISSING CODE>
i ← i + 1
}
The teacher has the following procedures available.Which of the following code segments can replace MISSING CODE so that the program works as intended? Select two answers.

gradeList[i] ← min (gradeList[i] + 5, 100)
gradeList[i] ← max (gradeList[i] + 5, 100)
gradeList[i] ← gradeList[i] + 5
IF (gradeList[i] > 100)
{
gradeList[i] ← gradeList[i] - 5
} gradeList[i] ← gradeList[i] + 5
IF (gradeList[i] > 100)
{
gradeList[i] ← 100
}Additional Sample Questions:
- I and II only
- Try asking a classmate for advice—s/he may be able to explain/suggest some ideas or recommend some strategies.
- I and III only
- This is correct. Only I and III are true.
- II and III only
- Try asking a classmate for advice—s/he may be able to explain/suggest some ideas or recommend some strategies.
- I, II, and III
- Try asking a classmate for advice—s/he may be able to explain/suggest some ideas or recommend some strategies.
Q-41: Which of the following are true statements about creating computational artifacts?I. A computational artifact must be created using a computer or computing device.II. A computational artifact must be created using a traditional, prescribed technique.III. Some computational artifacts are created by combining existing computational artifacts.
- All students must participate in all steps in the process of creating the video.
- This answer is correct.
- Flaws in the video are likely to be detected during the process, since team members will be reviewing the video regularly.
- In order to collaborate effectively, the students may need a method to resolve differences of opinion.
- The process facilitates the inclusion of multiple team members’ perspectives.
Q-42: A team of students is creating a video to advertise an upcoming school activity. While workingon the video, the students plan to meet every day to review their progress and plan next steps.Which of the following is a FALSE statement about the described collaborative process?
- I and II only
- This is correct
- I and III only
- II and III only
- I, II, and III
Q-43: Which of the following are true statements about digital audio files?I. An audio file can be created by using samples of one or more existing audio files.II. An audio file can be created by using a computer program to synthesize a new sound.III. An audio file that has gone through lossy compression can be restored to its original uncompressed version.
- A computer program that attempts to steal passwords and infect other computers
- A computer program that overloads a Web server with requests for resources
- An e-mail request for personal information from a user
- Software that looks for passwords by intercepting packets that are traveling across a network
Q-44: Which of the following is most likely to be part of a phishing attack?
- I and II only
- I and III only
- That's correct!
- II and III only
- I, II, and III
Q-45: Which of the following are true statements regarding the benefits of using e-mail to send messages? I. E-mail can be used to disseminate information to multiple recipients at once. II. E-mail is designed to be a completely secure way of sending confidential information. III. E-mail fosters communication and collaboration between people in distant locations.
- When the application is only shared with students at the same school
- When the application is shared on a peer-to-peer network
- When the student gets permission from the copyright owner of the application
- When the student makes a copy of the application for another student to use only once
Q-46: A student purchases a single-user license of a copyrighted application and wants other students to be able to use it at the same time. Under which of the following conditions is it considered acceptable for the student to share the application?
- II only
- I and III only
- II and III only
- I, II, and III
Q-47: Which of the following are true statements regarding the benefits of using the Internet tocommunicate? I. The Internet provides equal access to information across all socioeconomic groups globally. II. The Internet allows information to be disseminated to many people very quickly. III. The Internet fosters new ways to communicate and collaborate.
- Author
- Title
- Genre
- Quantity Available
Q-48: A bookstore has a database containing information about each book for sale in the store. A sample portion of the database is shown below.A store employee wants to calculate the total amount of money the store will receive if they sellall of the available science fiction books. Which columns in the database can be ignored and still allow the employee to perform this calculation? Select two answers.