
6.5. Caesar Cipher App¶
Time Estimate: 90 minutes
6.5.1. Introduction and Goals¶
| This lesson describes some basic terminology from the field of cryptography, and then introduces the Caesar Cipher, one of the earliest and simplest examples of a substitution cipher.
Once we understand how the Caesar algorithm works, we will implement it in a simple app that encrypts and decrypts messages. |
|
|
Learning Objectives: I will learn to
Language Objectives: I will be able to
|
|
6.5.2. Learning Activities¶
Part I: Introduction to Cryptography and the Caesar Cipher
Cryptography means secret writing. It is the art and science of sending secret messages and it has been used by generals and governments and everyday people practically since the invention of written language. As we will see in upcoming lessons, modern cryptographic techniques are essential to guaranteeing the security of our transactions on the Internet.
Cryptography plays a role whenever you make an online purchase at Amazon or provide your password to Google. Whenever you see the https protocol in your browser, you can rest assured that your communications are secure because they are being encrypted with strong, unbreakable encryption. If we couldn't rely on those transactions being secure we really wouldn't have the Internet as we know it today.
In upcoming lessons we will look at several different versions of cryptography, including the strong encryption that protects our Internet transactions. But let’s begin here with a simple cipher, the Caesar Cipher, so named because it was used by Julius Caesar in 1st century B.C. The following video will explain the basics of the Caesar Cipher. Click below to watch this presentation on Caesar Cipher.
Activity: Caesar Cipher
(Open widget in separate window)- Use the Caesar cipher to encrypt your name by hand using the cipher_alphabet below that is shift 3. Then use the widget above to check your answer.
PLAIN_ALPHABET: abcdefghijklmnopqrstuvwxyz CIPHER_ALPHABET: DEFGHIJKLMNOPQRSTUVWXYZABC
- Encrypt a short message for your partner by hand using the cipher alphabet with shift 3 above. Trade the encrypted messages and decrypt them by hand. Use the widget to check your answer.
- Create the CIPHER_ALPHABET that would result from a Caesar shift of 5. Use the widget above on some letters with shift 5 to check your answer.
- Try the self-check exercises below.
- a person who makes up secret codes
- This is challenging, but rewarding!
- an algorithm that is used to scramble text so that it can be passed in secret
- That's right! A cipher, such as the Caesar cipher, is an algorithm that is used to encrypt or scramble text so that it is unreadable unless one knows how to descrypt it. A cipher converts plaintext into ciphertext and vice versa.
- a lock that can be used to lock a message in a lock box
- This is challenging, but rewarding!
- any puzzle, such as a crossword or Sudoku puzzle
- This is challenging, but rewarding!
Q-2: A cipher is _________________________.
- transposition cipher
- Don’t worry, it’s hard! Let’s go back and try it again...
- bimodal cipher
- Don’t worry, it’s hard! Let’s go back and try it again...
- substitution cipher
- That's right! A cipher, such as the Caesar cipher, is an algorithm that is used to encrypt or scramble text so that it is unreadable unless one knows how to descrypt it. A cipher converts plaintext into ciphertext and vice versa.
- substantial cipher
- Don’t worry, it’s hard! Let’s go back and try it again...
Q-4: A Caesar cipher is an example of a ______________________.
Part II: Caesar Cipher App
To get started click on this link to open App Inventor and import the CaesarCipherTemplate. Use the Save As button to rename your project "CaesarCipherApp".
You are provided with a template that sets up the environment for implementing Caesar encryption and decryption. Your task will be to implement the encryption function following the tutorial and implement the decryption function as an enhancement.
Programming constructs you will learn in building this app are- Defining and using local variables
- Defining and using procedures with returns (also called functions)
- Using a for-each loop and an index to process a string of letters in a message
- Using built-in text functions to process a string of letters in a message
Functions and Local Variables
This app makes use of functions and local variables. A function is a procedure that returns a value. A local variable (in contrast to a global variable) is one that has a limited scope, which means that it only exists and can only be used within a block of code, for example in a procedure or a function. To help improve your understanding of these important programming concepts, there are several short (~ 1 minute) video tutorials available here.
In the AP exam, functions are represented in the following pseudocode compared to procedures and to App Inventor blocks:
| AP Text Pseudocode | AP Block Pseudocode | App Inventor Block | |
| Procedure |
PROCEDURE name(param1,...)
{
instructions
}
| 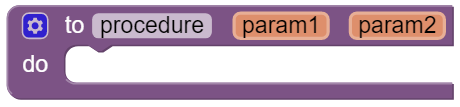 | |
| Function |
PROCEDURE name(param1,...)
{
instructions
RETURN (expression)
}
| 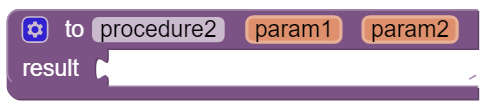 |
Enhancements and Extensions
- Decryption Implement the caesarDecrypt function and the handler for the decrypt button to enable the app to
perform decryption.
- Decryption is the mirror image of encryption. Whereas for encryption you replace every character in the plaintext with the corresponding letter from the CIPHER_ALPHABET, for decryption, loop through the ciphertext and replace every character with the corresponding letter from the PLAIN_ALPHABET.
- When you test the app, it will only work if you type lowercase letters into the plaintext textbox to encrypt, and type uppercase letters in the ciphertext textbox to decrypt.
- To fix this, in the ButtonDecrypt.Click, you could use
before calling your decrypt function.
- Extend the Alphabet As it is currently implemented, the plaintext alphabet consists only of lowercase letters 'a' through 'z'. This means that digits (0 through 9) and uppercase letters ('A' through 'Z') are not encrypted. That's a security flaw that makes it easier for Eve, the eavesdropper, to break the cipher and discover the secret message. To fix this, extend the plaintext alphabet to include digits and UPPERCASE letters in any order. If you use the appropriate amount of abstraction, this should be a simple change to implement!
- Challenging (Optional) Preserving the blank spaces between words makes it easier for Eve the eavesdropper to crack the encrypted message. To make this more difficult, write a function that will take a sentence and output the letters in four-letter blocks with all punctuation (i.e., all characters not in the plaintext alphabet) removed. For example, the function would take 'this, is a test message!!' return 'this isat estm essa ge'.
6.5.3. Summary¶
In this lesson, you learned how to:
6.5.4. Still Curious?¶
Read more about the historical context of Caesar's Cipher in Chapter 5 of Blown to Bits (pg.165).
6.5.5. Self-Check¶
Here is a table of some of the technical terms discussed in this lesson. Hover over the terms to review the definitions.
|
cipher
cryptography encryption plaintext ciphertext function |
decryption
encryption key encryption algorithm substitution cipher local variables |
Here are some Quizly exercises to practice coding functions.
6.5.6. Reflection: For Your Portfolio¶
Answer the following portfolio reflection questions as directed by your instructor. Questions are also available in this Google Doc where you may use File/Make a Copy to make your own editable copy.